The digital age is defined by speed, and few technologies embody this better than 5G. As the fifth generation of wireless networks, 5G is reshaping how people communicate, work, and access information. Its promise of lightning-fast connectivity, low latency, and the ability to connect billions of devices simultaneously has already begun to revolutionize industries and daily life. Yet, even as 5G continues its global rollout, researchers and engineers are already preparing for the future of connectivity—6G and beyond.
4G made mobile internet widely accessible, powering video streaming, social media, and app-driven lifestyles. But as technology demands grew—think smart homes, autonomous cars, and massive cloud platforms—4G’s limitations became clear. 5G stepped in with speeds up to 100 times faster than its predecessor and latency so low that real-time communication between devices became possible. This has opened new opportunities in areas such as telemedicine, remote work, and smart city infrastructure.
Transforming Industries with 5G
The impact of 5G extends far beyond personal convenience. Healthcare is one of the biggest beneficiaries, with surgeons now able to perform remote robotic operations thanks to ultra-reliable connections. In transportation, autonomous vehicles rely on 5G to communicate with each other and traffic systems, reducing accidents and congestion. Even entertainment has been transformed, with seamless augmented reality (AR) and virtual reality (VR) experiences becoming mainstream. The ability to connect millions of devices without lag has also fueled the Internet of Things (IoT), making homes and businesses smarter and more efficient.
The Road to 6G and Beyond
While 5G is still being deployed globally, the future of connectivity doesn’t stop there. Early discussions around 6G envision speeds up to 100 times faster than 5G, enabling technologies that seem futuristic today. Imagine holographic communication, fully immersive VR workplaces, and AI-driven cities where data flows seamlessly to improve daily life. Beyond 6G, innovations in satellite internet and quantum communications could make high-speed connectivity available even in the most remote corners of the world, bridging the global digital divide.
Connecting the World Faster and Smarter
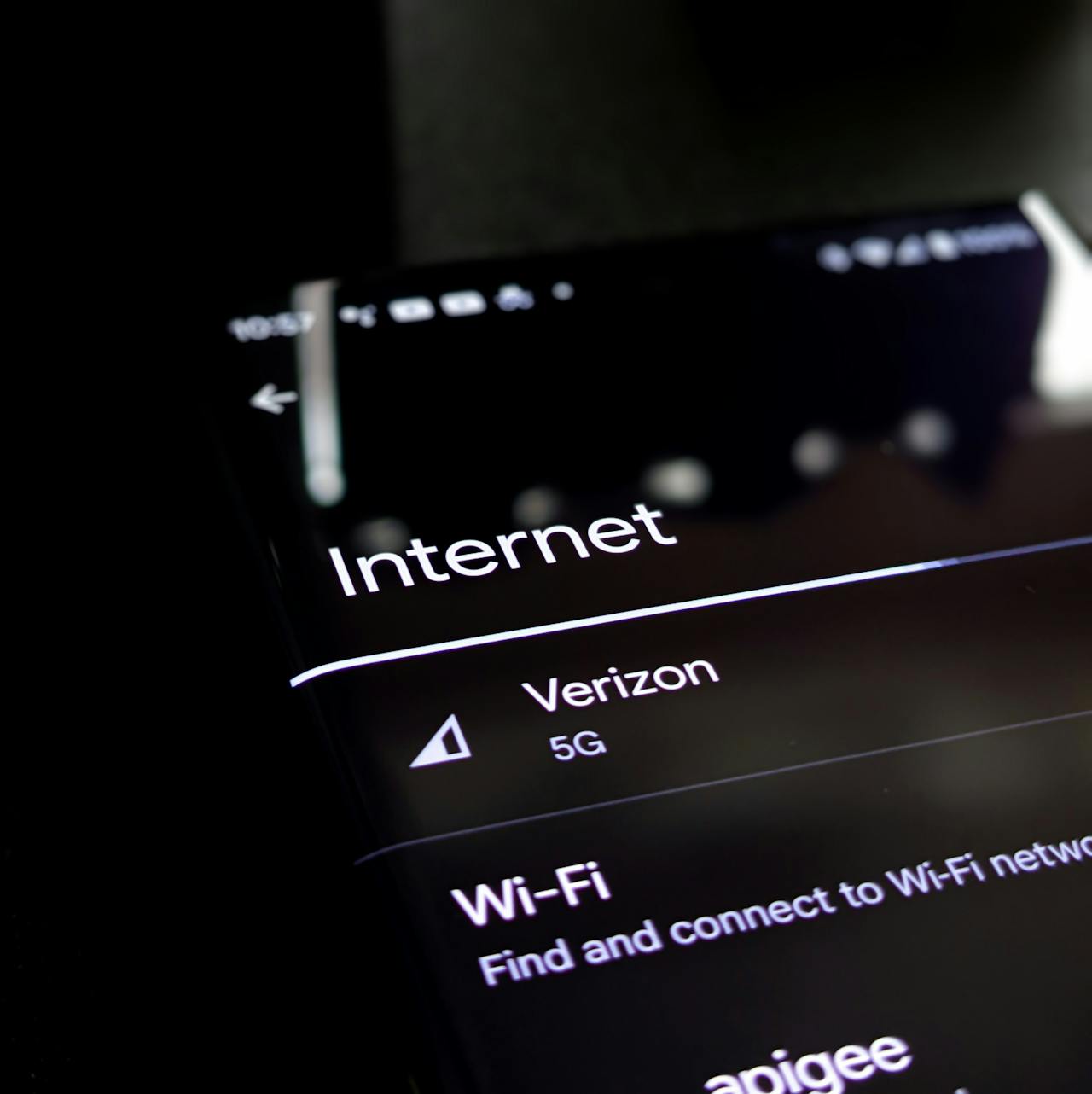
The real promise of 5G and beyond lies not only in speed but also in inclusivity. As coverage expands, developing nations gain access to opportunities previously limited to tech-driven economies. From online education to e-commerce and digital banking, faster networks are empowering individuals and businesses across the globe. The evolution of connectivity is not just about technology—it is about enabling global progress, collaboration, and innovation.
5G has already proven itself as a transformative force, powering innovations that were once science fiction. But it is just the beginning. With 6G and future technologies on the horizon, the world is moving toward an era of instant, seamless, and universal connectivity. As networks grow faster and smarter, they are not only changing how we communicate but also how we live, work, and create. In the journey from 5G to beyond, the world is truly becoming more connected than ever before.…


 Strong password policies should be the first line of defense against unauthorized access. With cybercriminals constantly searching for vulnerabilities, a weak password can be an open invitation. The application is pretty simple. Encourage employees to set up complex passwords that include a mix of symbols, letters, numbers, and even characters. This easily makes it harder for attackers to guess or crack them.
Strong password policies should be the first line of defense against unauthorized access. With cybercriminals constantly searching for vulnerabilities, a weak password can be an open invitation. The application is pretty simple. Encourage employees to set up complex passwords that include a mix of symbols, letters, numbers, and even characters. This easily makes it harder for attackers to guess or crack them. But again, cyber-attacks can sometimes be overkill. No updated technology can prevent some cyber-attacks. In this case, DLP can be your safety net. It involves strategies and tools designed to protect sensitive data from unauthorized access, even theft, or accidental loss. Implementing DLP means identifying where your data resides. This includes files on local drives, cloud storage, and email systems.
But again, cyber-attacks can sometimes be overkill. No updated technology can prevent some cyber-attacks. In this case, DLP can be your safety net. It involves strategies and tools designed to protect sensitive data from unauthorized access, even theft, or accidental loss. Implementing DLP means identifying where your data resides. This includes files on local drives, cloud storage, and email systems.
 Let’s start simple. Credit cards are probably the most common and safest way to purchase Instagram followers. When you use a credit card, your information is protected by law under the Fair Credit Billing Act of 1996. This ensures that if something goes wrong or someone attempts to steal your information, you can dispute any charges with your creditor and get them removed from your account. Additionally, credit cards provide you the added security of being able to dispute any charges if you don’t get the followers that were promised.
Let’s start simple. Credit cards are probably the most common and safest way to purchase Instagram followers. When you use a credit card, your information is protected by law under the Fair Credit Billing Act of 1996. This ensures that if something goes wrong or someone attempts to steal your information, you can dispute any charges with your creditor and get them removed from your account. Additionally, credit cards provide you the added security of being able to dispute any charges if you don’t get the followers that were promised.
 Sure, there is nothing wrong if you also opt for PayPal or Venmo, but when protecting your personal data, there is nothing like the almighty cryptocurrency. It may have been hyper-volatile in the past, but it is becoming widely accepted as a reliable form of payment across many industries.
Sure, there is nothing wrong if you also opt for PayPal or Venmo, but when protecting your personal data, there is nothing like the almighty cryptocurrency. It may have been hyper-volatile in the past, but it is becoming widely accepted as a reliable form of payment across many industries.